The WannaCry Ransomware Attack. What You Need to Know
Last Friday 12 May 2017, a large-scale ransomware attack affected hundreds of thousands of computers across the globe.
Aptly
named ‘WannaCry’, it has caused widespread disruption to many organisations,
including Nissan, FedEx and the UK’s National Health Service. According to
Europol, the attack was unprecedented in scale.
Keep
reading to find out what you need to know about WannaCry and other ransomware
attacks, and how you can protect your business from serious disruption.
What is ransomware?
Ransomware
is malicious software that encrypts files on your computer, preventing you from
being able to use them. It can also affect files that you share with others,
such as those stored on a file server or network attached storage (NAS). This
is an important point, as it may take only one computer in your network to
become infected in order to cause serious harm across the entire business.
Why is this malicious software called ‘ransomware’?
It’s
called ransomware because in order to recover your files, you need to pay a
ransom to the malware author. Normally you pay this using Bitcoin, which is
untraceable.
When
you pay the ransom, you will receive an unlock code which you can enter to
recover your files.
How does my computer become infected?
It’s
really easy. Usually you receive an email that contains an infected attachment,
or a link to a website. When you open the attachment or click on the link, your
computer becomes infected.
How do I know if my computer is infected?
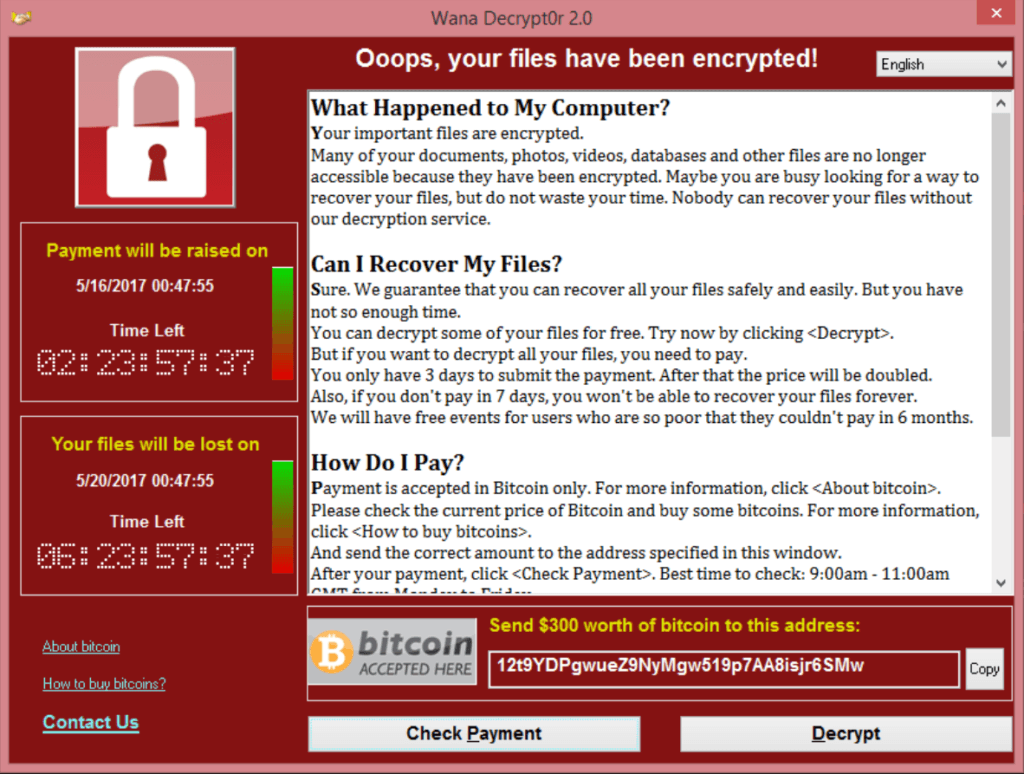
The
malware will display a message informing you that your files have been
encrypted, and advising you of how to pay the $300 ransom.
What happens if I don’t pay the $300 ransom?
If
you don’t pay the ransom within the required time, usually as little as 24 to
48 hours, the extortionist deletes the unlock code. It is then impossible to
decrypt your files. If you have a recent backup copy of your files, you may be
able to restore them from there. If you don’t have a backup, your files are lost
forever.
Should I pay the ransom?
We
don’t believe in rewarding people for criminal behaviour, so our answer is
usually a very strong ‘No.’ However if you don’t have a recent backup, paying
the ransom may be the only way to get your files back.
Although
paying the $300 ransom will enable you to recover your files, it leaves a
‘backdoor’ to your computer, potentially allowing it to be hacked in the
future.
How can I protect myself against ransomware?
Tip
1: Keep your operating system and application software up-to-date
Yes,
Internet access is expensive in Timor-Leste. But the cost of not patching your
system can be far greater.
The
WannaCry attack exploited a Windows security hole that Microsoft patched on 14
March 2017. WannaCry cannot infect systems that have been patched with all the
latest security fixes.
Although
anti-malware software is vital, it can only work reliably when your software
has been properly updated.
Tip
2: Use a leading anti-malware package and keep it up-to-date
We
use and recommend Bitdefender. In our testing we have found it to be the most
effective against the higher level of threats that we see in Timor-Leste.
Free
anti-malware software is largely ineffective, and you should avoid it.
Tip
3: Educate your users
Security
is everyone’s responsibility. Many malware attacks start with an email
containing an infected attachment or a link to a malicious website.
Users
should only click on links or open attachments from people that they know and
trust. Unfortunately, even that is not quite enough. Some malware sends emails
to everyone in a user’s contact list, so the email may look legitimate. If you
weren’t expecting an attachment from someone, it’s often wise to check with
them before opening it.
Tip
4: Keep effective backups
In
a business environment, you should backup all of your data at least every
night. Backups should be stored safely off-site. We can advise you on an
effective backup strategy and help you to implement it.
Tip
5: Personal devices should comply with organisational IT security policy
Most
infections that we see on business networks are introduced from personal
devices that belong to staff, contractors or visitors. These devices may not be
correctly patched, or they may not have proper anti-malware protection. This
places the business network at risk.
You
can avoid these dangers by requiring that personal devices comply with your
organisation’s security policy before they can be connected to the office
network. A better, low-cost method is to build a separate wireless network that
isolates personal devices from the business network, limiting the damage that
they can cause.
There
are many other options, and we can help you to choose which one will best suit
your budget and requirements.
Tip
6: Go professional – implement business-grade protection
Almost
all of our customers use centrally managed and monitored software updates and
anti-malware protection. This avoids the totally unreliable approach of having
all of your end-users managing their own updates (or disabling them entirely).
In our experience, unmanaged updates simply don’t work in a business
environment.
For
many of our customers, we have also implemented rock-solid protection that
constantly backs up changed files across the entire business.
Case study
One
of our Timor-Leste customers recently fell victim to a ransomware attack which
originated from a laptop belonging to an employee. Company policy permitted
staff-owned devices to access personal webmail, a practice we generally
recommend against. The attack originated in an infected email attachment, and
it encrypted mission-critical files in the organisation’s shared network
folders.
Within
one hour of the attack, we had recovered 100% of their lost files, up-to-date
as at 4 minutes prior to the attack. Without our business-grade data recovery
solution, they would have needed to restore from the previous night’s backup.
This would have taken many hours, with loss of the entire day’s work performed
since the previous backup.
Our
customer organisation has since tightened their security policy in line with
our advice.
The
best approach to security involves having multiple layers. A great deal of
protection can be implanted on even a small budget.
I have a Mac. I’m safe, right?
The
WannaCry ransomware exploits a specific Windows vulnerability, so it doesn’t
affect Macs. However most Mac users will have noticed that Apple frequently
issues security updates. All operating systems are vulnerable to malware
attacks. However because Windows is more widely used, malware developers
concentrate their efforts on attacking Windows.
Professional
security researchers advise that MacOS is not inherently more secure
than Windows. Therefore, Mac users still need to take the same steps to protect
themselves as what Windows users do. Mac users who believe, incorrectly, that
they do not need anti-malware protection are at greater risk than Windows users
who do use anti-malware.





Nice information...
ReplyDeleteelovia.biz